Information Security Solutions
- SIEM Solutions
- Virtual Private Network
- Email Security
- Data Protection
- Network Security
- System Security
- Penetration Testing
- Vulnerability Assessment
- ISMS Policy Templates
- ISO 27001 Consultancy
- BCP & DR Consultancy
- IT Audit consultancy
_________________________

_________________________
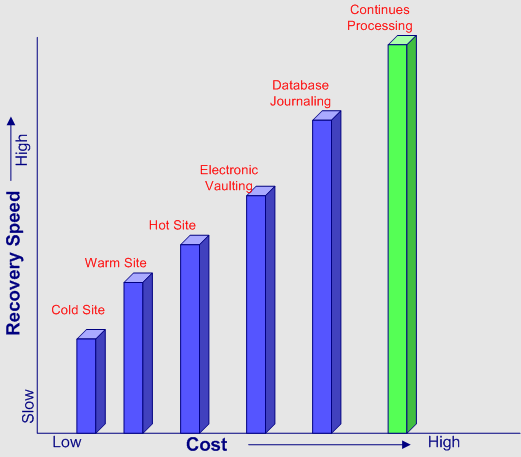
Recovery Strategy
"A way to recover systems and processes in case of interruption"
How to Select the Recovery Strategy?
- Criticality of the business process
- Applications supporting the processes
- Cost
- Time required to recover
- Security
iSquare Information Data Security Solutions
Data Security
To protect intellectual property and to identify, monitor, and protect valuable data
Methods to protect:
- Classify the data
- Measure the Risk
- Policy Adaption
- Compliance
- DLP Tools
Ways to protect Corporate Data
- Assess the inventory and risk
- Update systems with latest service patches and Signatures
- Use Firewall's and Anti virus program
- Implement ISMS policies
- Restrict downloading dubious software
- Access controls and authorization
- Block the removable mediums
Data Protection Tools
Safenet Solutions For:
- Commercial Data Protection
- Government Data Protection
- Software Rights Management
Safend
- Safend Protector is the industry's most comprehensive, secure and easy-to-use endpoint data leakage prevention solution
- Stop Information Leakage through Endpoints and Removable Media
Business Continuity Plan (BCP)
BCP is a system or methodology used to create a plan on how an organization will resume its partially or completely interrupted critical functions within a predetermined time after the occurrence of a disaster or disruption. The aim is to keep critical functions operational.
Business Impact Analysis:
BIA goal is to distinguish which are the most crucial and require to continue operations if a disaster occurs
Recovery point objective (RPO)—The RPO defines how current the data must be or how much data an organization can afford to lose. The greater the RPO, the more tolerant the process is to interruption.
Recovery time objective (RTO)—The RTO specifies the maximum elapsed time to
recover an application at an alternate site. The greater the RTO, the longer the
process can take to be restored